Network Edge simplifies connectivity by establishing a cloud on-ramp with single-hop adjacency to all the major cloud providers. With a single SD-WAN virtual appliance, multiple cloud environments can be seamlessly connected using consistent architecture.
As SD-WAN is adopted to provide scale, simplicity, and agility for corporate networks, the same principles need to be available for extending connectivity into the cloud. While virtual SD-WAN devices can be deployed in the cloud, there are scale and cost implications of replicating deployments across each cloud in each region. Compounding this issue is the requirement to understand the architectural and networking considerations for each cloud to effectively set up the devices.
Network Edge simplifies connectivity by establishing a cloud on-ramp with single-hop adjacency to all the major cloud providers. With a single virtual appliance, multiple cloud environments can be seamlessly connected, using the same consistent architecture. This approach provides the main benefits of the cloud (in terms of time to market and ease of deployment), but with one key distinction: it keeps the foundational networking outside of the cloud. This allows you to create a single control point for all cloud traffic, be it north-south between WAN and cloud, or east-west between clouds.
Architecture
The cloud on-ramp deployment in this reference architecture utilizes a single SD-WAN Network Edge appliance, connecting to three different CSPs, as well as to a Network Service Provider (NSP) for WAN connectivity.
Communication between all these different environments (CSPs and NSPs) is facilitated through private connectivity over Equinix Fabric. The inputs and options for establishing connectivity varies between cloud service providers but is well documented by each CSP.
Network Service Provider connectivity can be achieved through Software-Defined Interconnect (for select partners) or a physical hand-off using the Bring Your Own Connection (BYOC) workflow. Additional details on both will be available at the end of this document.
The SD-WAN appliance is responsible for both the termination of the overlay SD-WAN fabric on the WAN side, as well as the underlay routing to and between the different cloud environments.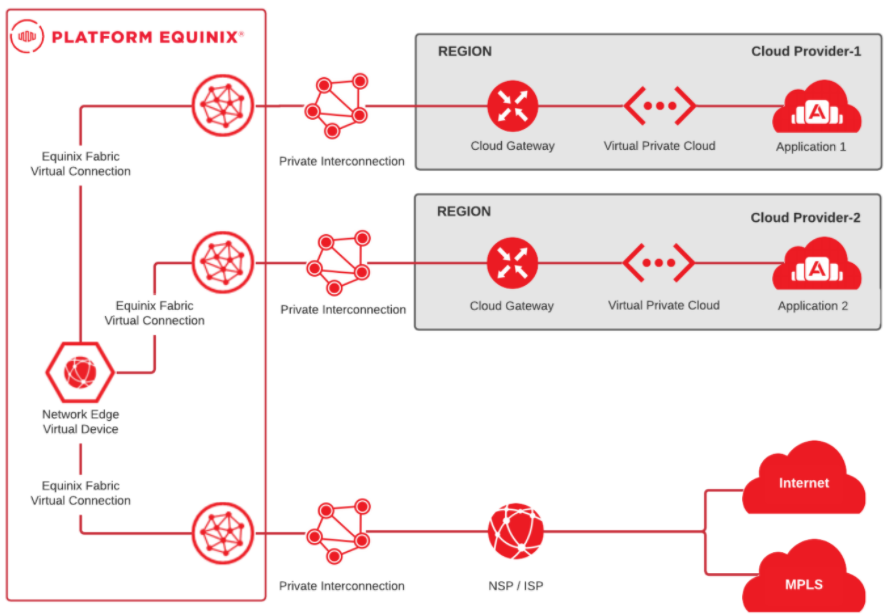
Equinix Components
-
Equinix Fabric – Equinix Fabric is a switching platform that provides private connectivity to a wide selection of providers that are participants on the Fabric. Virtual circuits are provisioned on the Fabric using software-defined networking to establish connectivity to providers that are connected to the Fabric. Virtual connections can be created using the Fabric Portal or APIs.
-
Equinix Network Edge – Network Edge is an ETSI-compliant NFV platform that hosts VNFs (routers, firewalls, and SD-WAN) from various vendors such as Cisco, Juniper, Palo Alto Networks, Fortinet, Versa, Aruba, and Check Point. VNFs can be deployed in real-time and, once deployed, you can start building virtual connections to providers on the Fabric.
Cloud Service Provider (CSP) Components
-
Private interconnection – Private interconnections from the CSP are Layer 2 partner or hosted connections that connect to the Equinix Fabric. Partner or hosted connections provide an intermediate switch between a device and the CSP router it peers with. Once the private Layer 2 interconnection has been established, you can set up Layer 3 peering with the CSP gateway. Private interconnections bypass the internet.
-
Cloud gateway – The cloud gateway is a software-defined router that is instantiated in the CSP network and connected to the virtual private cloud. The cloud gateway is used to establish BGP peering to the Network Edge device and is attached to the virtual private cloud (VPC) providing reachability between clouds.
-
Virtual private cloud – The VPC is a virtual network that serves as the container to deploy subnets and other networking constructs to instantiate compute and other application services.
Network Service Provider
-
Private interconnection – Depending on the level of integration that a NSP has with Equinix Fabric, connectivity can either be through a software-defined interconnect (for select, pre-integrated providers) or the BYOC workflow (for service providers who are not integrated into Fabric). Customers are still required to maintain a contract/arrangement with the NSP for connectivity beyond the private interconnection facilitated by Equinix Fabric.
Recommendations
These recommendations provide a starting point. Customer requirements might differ from this list.
Choice of location
-
One important key to interconnection is proximity to the resources that are being consumed. In relation to this architecture, this means the proximity of Network Edge infrastructure to the NSP and CSP edges. Not every CSP has an on-ramp in every location – the same applies for the edges of a NSP’s network and Network Edge infrastructure.
-
To keep the network latency as low as possible, it's recommended that you select a metro that has the best interconnection to the providers that you need. See the Equinix Service Provider list to learn more about which providers are local to which metros.
-
See the Network Edge Data Sheet for information about locations.
High Availability
-
This high-level design shows a single end-to-end connection from NSP, to virtual appliance, to cloud.
-
Some CSPs (such as Microsoft Azure ExpressRoute) mandate redundant private connectivity. This presents as two virtual circuits within the Equinix Fabric. While both circuits can be connected to a single virtual appliance, there are considerations around creating VNF-level diversity
-
Network Edge offers the ability for high availability and clustered (for select VNFs) appliance deployment models.
-
Careful consideration should be given to the design of solutions to ensure that service impacting events are minimized.
Network CIDR blocks
To avoid requirements around NAT (network address translation) / PAT (port address translation), select CIDR blocks that don't overlap with any other network to which you intend to set up private connections.
Considerations
When implementing this architecture, consider the following factors:
Performance
In addition to latency, bandwidth between the components and device throughput must is important. The virtual circuits must be sized appropriately, and the devices must support the desired throughput.
Security
Private interconnections on the Fabric to the cloud provider are not encrypted. An application that requires encryption must encrypt either at the application layer, or at the network layer where IPSEC tunnels can be built between the Network Edge device and a cloud gateway. IPSEC tunnels involve overhead, which also affects the device selection.
Equinix Costs
-
Device instance – The cost for the virtual device (does not include the license cost).
-
License for the virtual device – Customers can purchase a subscription license for some vendors. Bring Your Own License (BYOL) is available for all vendors.
-
Virtual circuits – Monthly recurring charges are based on the size of the circuits. Connections between metros across the Equinix Fabric, incur an additional surcharge for the remote connection.
-
Equinix Fabric port – Charged if BYOC is used to connect to NSPs/ISPs.
CSP Costs
-
Egress Charges – Charged by some service providers based on the amount of data that is transmitted over the private interconnection. These charges vary based on the provider. Using a private interconnection reduces the egress charges when compared to the Internet.
-
Private Connectivity Charges – Charged monthly by some providers for the private circuit into their environment. Both egress and private connectivity charges factor into your application design.
Scalability
-
Even though this reference architecture focuses on two different CSP environments, the virtual appliance in Network Edge can connect to any destination on Equinix Fabric. This allows for additional destinations to be connected using the same model highlighted above.
-
The limiting factor for the scalability of a single appliance is the number of virtual interfaces supported, as well as the throughput for high bandwidth environments.

