Network Edge works with Equinix Fabric to provide a virtual cloud on-ramp that can be spun up in minutes. This provides low-latency hybrid multi-cloud access for a variety of applications. If the applications are multi-tiered or latency-sensitive and need access to enterprise resources, they can be implemented using a virtual security device deployed on Network Edge at a single control point.
Architecture
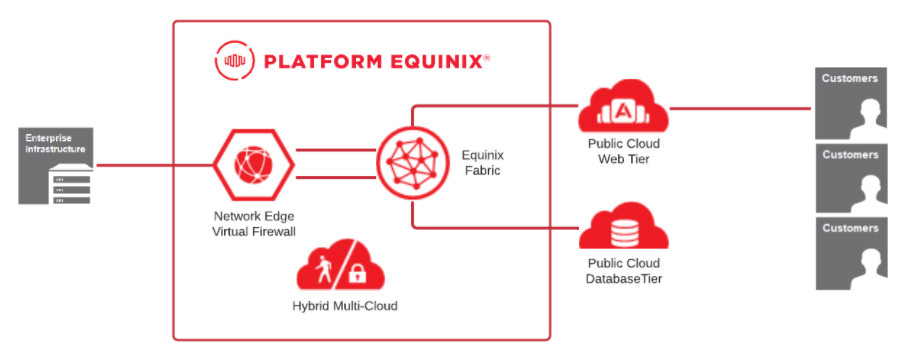
The hybrid multi-cloud topology in this reference architecture scenario has a web tier deployed in one cloud provider and a database tier deployed with another cloud provider in the same region. The only publicly accessible component of the application is the web tier. All other components must be secured, including the Enterprise infrastructure which also provides services to the application and must be near the other components due to latency requirements.
This solution reduces the number of deployed devices and creates a single security control point between all the application tiers. For enterprises, network complexity is reduced, which, lowers costs for cloud-to-cloud connectivity and enhances security.
Network communication between the application tiers is provided by direct private Layer 2 interconnections over the Equinix Fabric, with the Network Edge device providing Layer 3 routing and security services. The Network Edge device is a virtual network function (VNF) that is hosted by the Network Edge network function virtualization (NFV) platform.
Equinix Components
-
Equinix Fabric – Equinix Fabric is a switching platform that provides private connectivity to a wide selection of providers that are participants on the Fabric. Virtual circuits are provisioned on the Fabric using software-defined networking to establish connectivity to providers that are connected to the Fabric. Virtual connections can be created using the Fabric Portal or APIs.
-
Equinix Network Edge – Network Edge is an ETSI-compliant NFV platform that hosts VNFs (routers, firewalls, and SD-WAN) from various vendors such as Cisco, Juniper, Palo Alto, Fortinet, Versa, Aruba, and Check Point. VNFs can be deployed in real-time and, once deployed, you can start building virtual connections to providers on the Fabric.
Application Components
-
Private interconnection – Private interconnections from the Cloud service provider (CSP) are Layer 2 partner or hosted connections that connect to the Equinix Fabric. Partner or hosted connections provide an intermediate switch between a device and the CSP router it peers with. Once the private Layer 2 interconnection has been established, you can set up Layer 3 peering with the CSP gateway. Private interconnections bypass the internet.
-
Public cloud web tier – The public cloud web tier hosts the web servers that are exposed on the public internet for user connectivity. This tier also provides internet services which are provided either by the public cloud provider or by an internet service provider that is on the Fabric.
-
Public cloud database tier – The public cloud database tier hosts the database PaaS services that are interconnected to the web tier. This tier is protected by the virtual security device, because traffic between the web tier and database tier must traverse the security control point.
-
Enterprise infrastructure – The enterprise infrastructure hosts private services for the application. This infrastructure can be hosted in an Equinix data center, provided by Equinix Metal, or hosted at another location. The only requirement is that Equinix Fabric be able to reach the infrastructure.
Recommendations
These recommendations provide a starting point. Customer requirements might differ from this list.
-
Choice of location – This architecture example shows connections between the same region. Depending on the region for deployment, latency will vary, which is an important consideration when designing applications with stringent latency requirements. However, some applications might require inter-region connectivity. In those cases, use the global reach of Equinix Fabric to create those connections.
-
High Availability – This architecture shows a single-threaded deployment with no fault-tolerance. Equinix recommends that customers deploy the level of fault -tolerance needed for their business requirements. Network Edge can be deployed with redundant devices or, in the case of some vendors, devices be deployed as a high-availability pair.
-
Network addressing – For connections to private services over a private virtual interface, customers can use private IP addressing. For some public services, the customer’s own public IP addresses and NAT might be required for the Network Edge device. Because each CSP is different when it comes to public addressing requirements, research is required before trying to create public connections. For the web tier, customers can either bring their own IP addresses that meet internet advertisement requirements, or use provider-assigned addressing.
Considerations
When implementing this architecture, consider the following factors.
Performance
In addition to latency, bandwidth between the components and device throughput must is important. The virtual circuits must be sized appropriately, and the devices must support the desired throughput.
Security
Private interconnections on the Fabric to the cloud provider are not encrypted. An application that requires encryption must encrypt either at the application layer, or at the network layer where IPSEC tunnels can be built between the Network Edge device and a cloud gateway. IPSEC tunnels involve overhead, which also affects the device selection. This solution deploys a virtual security device at a single control point that intersects all traffic flows between the application tiers.
Equinix Costs
-
Device instance – The cost for the virtual device (does not include the license cost).
-
License for the virtual device – Customers can purchase a subscription license for some vendors. Bring Your Own License (BYOL) is available for all vendors.
-
Virtual circuits – Monthly recurring charges are based on the size of the circuits. Connections between metros across the Equinix Fabric, incur an additional surcharge for the remote connection.
CSP Costs
-
Egress Charges – Charged by some service providers based on the amount of data that is transmitted over the private interconnection. These charges vary based on the provider. Using a private interconnection reduces the egress charges when compared to the Internet.
-
Fixed Port Charges – Charged by some providers based on the circuit size, in addition to the egress charges. Both egress and fixed port charges factor into your application design.
By deploying a virtual security device on Network Edge, customers can consolidate hybrid multi-cloud connections at a single security control point, while maximizing application performance and enhancing security.

