User Access is a generic service (available with most vendors) that provides direct access to the device. It can take several forms; the most common is SSH.
Secure Shell, or SSH, is a common access method that allows approved users to log into the device and operate on it directly. SSH credentials can be added for up to a number of users. Equinix will restrict some activities of the SSH user to prevent major accidents or lockouts from occurring, but we try, where able, to minimize this restriction. For example, an SSH user would not be able to delete the SSH interface. This keeps both Equinix operational visibility and the customer’s own users from being locked out of the device with no way to resolve other than a complete delete.
The user access service has the following attributes:
|
Values |
Data Requirements |
Notes |
|
|---|---|---|---|
|
Configure before launch: |
Yes* |
|
* Users who have been defined for previous devices can be used for this one. |
|
Configure at launch: |
Yes |
Option located in Additional Services section of new device. |
|
|
Configure during lifecycle: |
Yes |
Option located on Additional Services tab in Device Details. |
|
|
Optional or Required |
Optional |
||
|
Username |
Required (w/ password) |
Must be at least 3 characters and max 32; must be unique to the market |
Can add new (w/ password) or select from list of existing users. |
|
Password |
Required |
Must be at least 6 characters and max 12; can include lower and upper-case letters, numbers, and some special characters |
Only defined when creating a new user for first time. The user can't re-enter the same or new password for an existing user. |
|
Device |
UUID; Required |
Alphanumeric |
On the portal, the device UUID is assumed based on the currently active device that user is viewing. |
|
How many users per device |
5 |
|
|
|
How many users per account |
See notes |
Number of deployed devices x5 |
|
|
Required same on secondary? |
No |
Can have no user access, same or different. |
Some vendors offer a basic user interface loads when navigating to the address or FQDN of the device. The user access service can be used for this purpose, as well, because typically it's a shell over SSH or the CLI already.
When a user logs into the device directly through SSH, they typically use a client such as Telnet, PuTTY or OpenSSH. This will grant them access to the CLI of the device. Equinix adds user permission limitations to prevent catastrophic errors, yet we try to allow as much as possible. Some vendors do not have the ability to limit user controls to SSH.
As a result, the customer assumes all responsibility for configuration changes and adjustments that they commit to the device. Any resulting impairment or outages might not apply to the SLA guarantee. The customer also assumes all responsibility for understanding how to navigate and configure that device using the appropriate OS and version for that vendor.
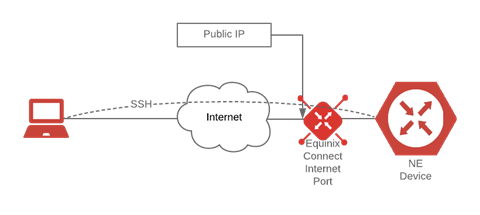
Users can see and operate on nearly all aspects of the device, just as they would a physical device inside their corporate network. For example, when logged into the device, the user can show the interfaces (with the appropriate command for that vendor and OS) and will see the SSH interface, which always includes a public IPv4 address issued by Equinix. Read more about interfaces on your device, in the Device Configuration section of the Deployment Guide.
Warning: If you are not comfortable making changes directly to the device rather than through the Equinix portal or API, do not enable this service
When adding user access to an HA pair, the user must elect if they want to duplicate the same user privileges on the secondary device or add a different list of users.
User Access service allows you to enter up to 5 user names and associated passwords per device. The same username/password combo can be repeated in more than one device, if desired, but must be unique within a single Equinix metro.
Note: Equinix user credentials are mutually exclusive to the settings and data on this virtual device. It's not related to, nor will it impact or change any user credentials related to the Equinix Fabric portal or any other Equinix portal, system or property. Therefore, customers can enter users for device access that are not also users of any other Equinix-related tool. Further, if the user wishes to access the device, he must create a user and password in this service; his Equinix credentials will not work for direct access. If a user decides to add credentials that are the same as Equinix user credentials, this is coincidental and there is no synchronization.
Each time a user is entered, changed or deleted, and SAVE is clicked, the full set of user configurations is immediately pushed to the device and Equinix TACACs server, where relevant.
To allow access to work properly, users should coordinate it with ACLs to ensure the accessing addresses are allowed.

