Networking
The Equinix Hybrid Cloud environment allows creating virtual networks and capabilities to enable communication between VMs and services needed in the Cloud, including the following components.
Network Types
- Isolated Network – Internal networks are available in the source VDC (Dedicated, Flex, or On-Demand), without external routing to other services or VDCs.
- Routed Network – Routable networks are available in the VDC (Dedicated, Flex, or On-Demand) with default routing between VDCs and external Cloud communication if pre-configured through firewall rules and BGP routing policies on the user's edge devices.
Edge Gateways
Internal routers used in the communication of networks are routed between VDCs or external Cloud networks. This capability is pre-configured by Equinix and connected to a VRF-TierO (Virtual Routing and Forwarding) dedicated to the user in high availability, with BGP routing for external Cloud communication. Its configuration is carried out based on a technical survey of Firewall or Managed Services L3, when contracted along with the Equinix Hybrid Cloud offering.
In addition to the Network Hardware L3 products available in Equinix’s standard portfolio, you can opt for the connection of Edge Gateways and VRF-TierO through an existing environment, if your equipment meets the BGP protocol support and connection prerequisites.
Firewall, NAT, and External Networks
The Edge Gateway (Tier-1) provides the Gateway Firewall (North-south -layer 7) and NAT (Network Address Translated) features by default, working on the VDC edge. This allows or denies communication between your virtual Data Centers, and external Cloud communication.
Networks can be classified as inbound or outbound ports for internal routed networks. They are pre-configured by Equinix based on the contracted connectivity product technical survey, and used when the Nat service is enabled. This masks access of an internal routed network at the connection’s entry or exit.
Despite the native L4 firewall feature in the Hybrid cloud solution in the Tier-1 layer, it does not replace the need for an edge firewall with BGP routing support, with available communication with VRF-TierO and support for layer-7 security features, if contracted.
Creating and Editing Firewall Rules
On the main page of the Hybrid Cloud portal, go to Networking → Edge Gateways, then click the Edge Gateway associated with the desired VDC. Confirm the type of external service connected to the Hybrid Cloud edge (Managed Services or Managed Firewall).
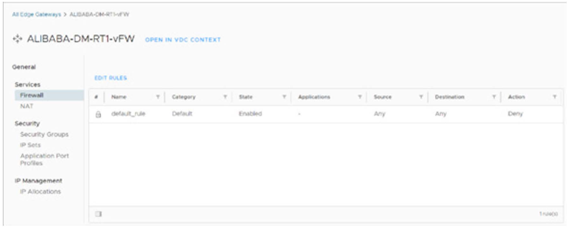
On the next screen, select Services → Firewall and review the default rule. Add or manage new rules using the EDIT RULES button.
Through the Security menu, you can create security groups, IPs, and services to simplify rule management.
Microsegmentation – VDC-Group (End of Sales)
This feature entered End of Sales on May 29, 2024. It is only available for customers who were active before this date. Customers who contracted Hybrid Cloud after this date cannot use this feature.
The Virtual Datacenter Group (VDC-Group) allows grouping of VDCs and enables Distributed Firewall functionality for microsegmentation. This provides segmentation of virtual machines based on names and attributes and supports sharing networks between Dedicated, Flex, and On-Demand clusters.
The Distributed Firewall is built into the hypervisor kernel, offering visibility and control for workloads and virtualized networks. You can create access control policies based on objects such as VM names and networks (IP addresses or IP sets). Firewall rules are applied at the vNIC level of each VM, ensuring consistent access control even during vMotion migrations. This supports a microsegmentation security model where East-West traffic can be inspected up to Layer 7.
Activation of VDC-Group can be requested when creating a new environment. For existing environments, open a support ticket so Equinix can perform a requirements assessment and impact analysis before enabling the feature.
Creating and Editing Networks with VDC-Group
After enabling the microsegmentation feature, a new tab called Data Center Group will appear, showing the grouping of VDCs. To create a new network, select the Data Center Group option, where the networks will be automatically shared among the VDCs.
Distributed Firewall – Creating and Editing Rules
To create security policies in the Distributed Firewall, go to Networking → Data Center Groups in the Hybrid Cloud portal.
Open the VDC-Group for your tenant, then select Distributed Firewall → Edit Rules.
Creating and Editing NAT Rules
The NAT service is optional and should be considered based on your environment’s topology. Common use cases:
- Use Case 1: NAT occurs on the external edge firewall outside Hybrid Cloud, connected to VRF-Tier0. In this case, NAT and External Network features in EdgeGateway-Tier1 are not required.
- Use Case 2: NAT occurs on the EdgeGateway-Tier1 of the VDC using a range of public IPs reserved for the customer.
- Use Case 3: Chained NAT: external firewall performs NAT to VRF-Tier0, then EdgeGateway-Tier1 performs a second NAT to an internal routed network.
For Use Cases 2 and 3, add new NAT rules (DNAT and SNAT) via Services → NAT, then click NEW.
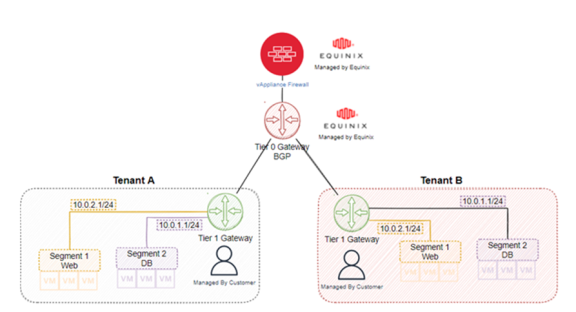
Edge Gateways – High-Level Topology
Next is a high-level topology to help clarify internal and external connections to the Hybrid Cloud.
- Tier-0 Gateway – These VRF-Edge routers are responsible for the BGP link with the external environment to the Hybrid Cloud, and internal routing between VDCs. It is configured by Equinix based on the technical survey of the contracted services and connectivity solutions.
- Tier-1 Gateway – Classified as Edge Gateway in the Hybrid Cloud Portal, this is responsible for the connection and routing of networks, DHCP, Gateway Firewall and VDC Nat services. Initially configured by the Equinix enablement team, it is based on the technical survey of the contracted services and connectivity solutions.
- Segment – This is classified as Network in the Hybrid Cloud Portal, with the options of Internal Network or Routed Network. Its creation and configuration can be carried out by the user, and subsequently cleared through routing policies and firewall rules available at the Cloud edge.
Create and Edit Virtual Networks
Some virtual networks are created by the Equinix enablement team by default, based on the technical survey of the connectivity product or professional service contracted with the solution. However, new networks can be created and routed at any time to meet new demands.
On the home page of the Equinix Hybrid Cloud Portal, access Networking | Networks, and click New.
| New Organization VDC Network | ||
|---|---|---|
| Scope | Select the desired VDC and click Next. | In this case we can choose to create networks in the Dedicated, Flex or On-Demand Virtual Datacenter. |
| Network Type | Select the type of network you want, opting for a routed or isolated connection | Each VDC can contain up to two routers in the routed connection model, one dedicated for connecting to external networks and the Internet and the other specifically for connecting to the Equinix services network, delivering products such as “Backup”, “Intelligent Data” and others. |
| General | Enter a name, CIDR Gateway and Description. | For example: LAN01, 192.168.110.1/24 |
| Static IP Pools | Enter a pool of IPs available for automatic allocation when creating new VMs | For example: 192.168.10.100-192.168.110.100 |
| DNS | Enter the primary, secondary and Suffix DNS addresses | For example: 8.8.8.8, 8.8.4.4, domain.local |
| Ready to complete | Review options and confirm the creation of the new virtual network. |
Networks are routed internally between the VDCs by default. However, the BGP routing policies and firewall rules must be reviewed to enable external access and internet access. This additional configuration can be requested to our support team when the user’s edge firewall is managed, or can be configured by the user himself when the firewall is not managed. Optionally, non-managed customers can also contract technical hours to clear and create routing and firewall policies.
Create and Edit Firewall Rules
-
On the home page of the Equinix Hybrid Cloud Portal, click Networking | Edge Gateways.
-
Select the Edge Gateway related to the desired VDC, also based on the type of external service associated to the Hybrid Cloud edge (Managed Services or Managed Firewall).
-
On the next screen, click the Services -> Firewall menu, and check the default environment rule. Click EDIT RULES to add and manage new rules.
-
In the Security menu, create security groups, IPs, and services to facilitate rule management.
Security Groups Create security groups and add the networks used by the VMs in the VDC. For example: SC-LAN-ONDEMAND (Will encompass all VMs connected to that network). IP Sets Create IP groups to identify networks external to the VDC. Application Port Profiles Create services to identify the applications and ports used.
Create and Edit NAT Rules
The NAT service is optional and its use must be considered based on the environment’s topology. Some use cases are listed as follows:
- Use Case 1 – Addresses can be translated directly in the edge firewall external to the Hybrid Cloud, which is connected to VRF-Tier0. It delivers a translated communication to internal routed networks. In this scenario, the NAT and external Network features of the EdgeGateway-TierI of the VDC are not required.
- Use Case 2 – The external VDC network may contain a range of public IPs reserved for the user. In this case, the NAT may occur directly in the EdgeGateway-Tierl of the VDC, masking an internal routed network.
- Use Case 3 – This use case occurs when a NAT is linked to another NAT. That is, a public network connected to a firewall external to the Hybrid Cloud and VRF-Tier0. It performs a NAT for another external network with private IPs in the EdgeGateway-Tierl of the VDC, which performs a second NAT to an internal routed network.
In Use Cases 2 and 3 listed above, you can add new NAT rules (DNAT and SNAT) through Services -> NAT, by selecting NEW.