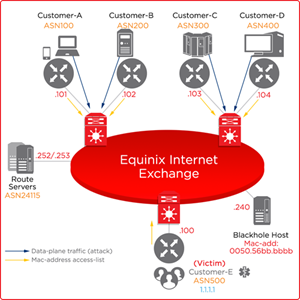
Remotely Triggered Black Hole Services
Remotely Triggered Black Hole (RTBH) filtering is a self-managed feature that enables you to block unnecessary traffic before it enters Equinix Internet Exchange (IX) protected network. RTBH protects you from Distributed Denial of Service (DDoS) attacks.
-
Equinix provides Black Hole Host with IP address .240 (in APAC), or .253 (in AMER and EMEA) on the IX subnet with mac address 0050.56bb.bbbb.
-
All unicast traffic towards the Black Hole Host is denied at customer facing ports (by mac-address ACL).
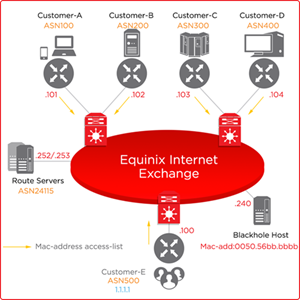
For filtering to take effect, the Black Hole announcement must be accepted by other peering partners. Peering participants can accept the prefixes with prefix length = 32 and BGP community 65535:666. Participation in the RTBH feature is optional.
Host Information
AMER
| Metro | IPv4 Address | IPv6 Address | Mac Address |
|---|---|---|---|
| Atlanta | 198.32.182.253 | 2001:504:10::2:4115:253 | dead:dead:dead |
| Chicago | 208:115:137.253 | 2001:504:0::2:4115:253 | dead:dead:dead |
| Dallas | 206.223.118.253 | 2001:504:0::2:4115:253 | dead:dead:dead |
| Washington DC | 206.126.239.253 | 2001:504:0::2:4115:253 | dead:dead:dead |
| VA | 198.32.190.253 | 2001:504:e::2:4115:253 | dead:dead:dead |
| Denver | 198.32.114.253 | 2001:504:0::2:4115:253 | dead:dead:dead |
| Houston | 198.32.135.253 | 2001:504:0::2:4115:253 | dead:dead:dead |
| Los Angeles | 206.223.123.253 | 2001:504:0::2:4115:253 | dead:dead:dead |
| Miami | 198.32.242.253 | 2001:504:0::2:4115:253 | dead:dead:dead |
| Miami | 198.32.114.253 | 2001:504:0::2:4115:253 | dead:dead:dead |
| New York | 198.32.118.253 | 2001:504:f::2:4115:253 | dead:dead:dead |
| Seattle | 198.32.134.253 | 2001:504:12::2:4115:253 | dead:dead:dead |
| Silicon Valley | 206.223.117.253 | 2001:504:0::2:4115:253 | dead:dead:dead |
| Portland | 198.32.176.253 | 2001:504:d::2:4115:253 | dead:dead:dead |
| Toronto | 198.32.181.253 | 2001:504:d::2:4115:253 | dead:dead:dead |
| São Paulo | 64.191.232.253 | 2001:504:0:7:0:2:4115:253 | dead:dead:dead |
APAC
| Metro | IPv4 Address | IPv6 Address | MAC Address |
|---|---|---|---|
| Hong Kong | 119.27.63.240 | 2001:de8:7::2:4115:240 | 0050.56bb.bbbb |
| Melbourne | 183.177.61.240 | 2001:de8:6:1:0:2:4115:240 | 0050.56bb.bbbb |
| Osaka | 203.190.227.240 | 2001:de8:5:1:0:2:4115:240 | 0050.56bb.bbbb |
| Perth | 101.97.43.240 | 2001:de8:6:2:0:2:4115:240 | 0050.56bb.bbbb |
| Singapore | 27.111.231.240 | 2001:de8:4::2:4115:240 | 0050.56bb.bbbb |
| Sydney | 45.127.175.240 | 2001:de8:6::2:4115:240 | 0050.56bb.bbbb |
| Tokyo | 203.190.230.240 | 2001:de8:5::2:4115:240 | 0050.56bb.bbbb |
EMEA
| Metro | IPv4 Address | IPv6 Address | MAC Address |
|---|---|---|---|
| Amsterdam | 185.1.112.253 | 2001:7f8:83::2:4115:253 | dead:dead:dead |
| Dublin | 185.1.109.253 | 2001:7f8:c3::2:4115:253 | dead:dead:dead |
| Frankfurt | 185.1.102.253 | 2001:7f8:bd::2:4115:253 | dead:dead:dead |
| Geneva | 192.65.185.253 | 2001:7f8:1c:24a::2:4115:253 | dead:dead:dead |
| Helsinki | 185.1.86.253 | 2001:7f8:af:0::2:4115:253 | dead:dead:dead |
| London | 185.1.104.253 | 2001:7f8:be::2:4115:253 | dead:dead:dead |
| Lisbon | 185.1.116.253 | 2001:7f8:c7::2:4115:253 | dead:dead:dead |
| Manchester | 185.1.101.253 | 2001:7f8:bc::2:4115:253 | dead:dead:dead |
| Madrid | 185.1.22.253 | 2001:7f8:c6::2:4115:253 | dead:dead:dead |
| Milan | 185.1.106.253 | 2001:7f8:c0::2:4115:253 | dead:dead:dead |
| Paris | 195.42.144.253 | 2001:7f8:43:0::2:4115:253 | dead:dead:dead |
| Stockholm | 185.1.107.253 | 2001:7f8:c1::2:4115:253 | dead:dead:dead |
| Zurich | 194.42.48.253 | 2001:7f8:c:8235::2:4115:253 | dead:dead:dead |
Other Supported BGP Communities
Log in required.
| Definition | Community String |
|---|---|
| Default Open Policy – Announce to all except to AS12345 | 24115:24115 0:12345 |
| Default Closed Policy – Announce to none except to AS12345 | 0:24115 24115:12345 |
| Prepend once to AS12345 | 65501:12345 |
| Prepend twice to AS12345 | 65502:12345 |
| Prepend three times to AS12345 | 65503:12345 |
| Black Hole Traffic | 65535:666 |
Distributed Denial of Service Attacks
Distributed Denial of Service (DDoS) attack causes disruption of services due to unnecessary inbound traffic in your port. RTBH filtering can help to free the port utilization from this unnecessary traffic.
To free the port utilization, the Equinix MLPE route server inserts a BGP route into the network that forces the routers to stop all traffic to the Black Hole Host with predefined IP and MAC addresses.
Before the DDoS Attack Begins
- Establish BGP peering to MLPE route servers through MLPE IX peering subnet. You can announce your prefix 1.1.1.0/24 to MLPE route servers.
- MLPE route servers re-announce your prefix to other peering participants.
- The next hop to reach 1.1.1.0/24 prefix is .100 which is your peering IP address.
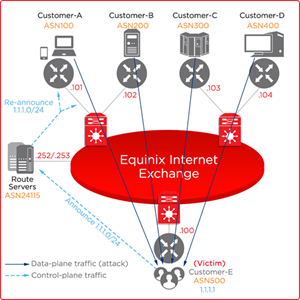
When the DDoS Attack Begins
-
There is a DDoS attack traffic towards the server 1.1.1.1.
-
Your port is flooded with inbound traffic causing service disruption to all production services.
-
Free the port utilization by stopping traffic to 1.1.1.1.
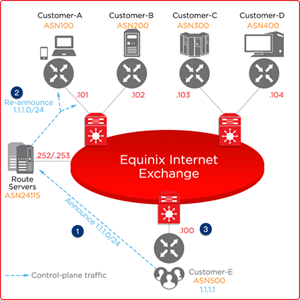
Mitigating DDoS Risks
To mitigate the risk of DDoS attacks:
Mitigation Stage 1
-
You announce 1.1.1.1/32 with Black Hole BGP community 65535:666.
-
MLPE route servers modify these prefix announcements (tagged with 65535:666) with next-hop to .240 (in APAC) or .253 (in AMER and EMEA), and re-announce the same prefix to other peering participants.
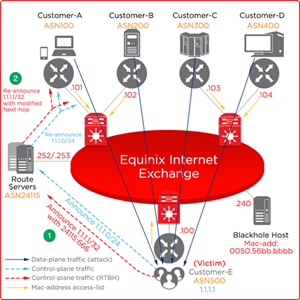
Mitigation Stage 2
-
Peering partners start to resolve next-hop IP address .240 (in APAC) or .253 (in AMER and EMEA) to reach 1.1.1.1.
-
Black Hole Host replies with an ARP with mac-address 0050.56bb.bbbb.
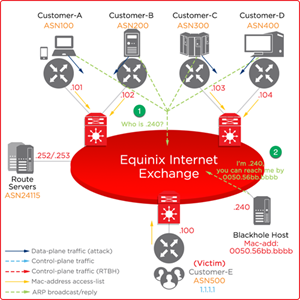
Mitigation Success
-
The attack traffic with next-hop .240 (in APAC) or .253 (in AMER and EMEA) is stopped by Equinix IX switch inbound access list.
-
The DDoS attack going through your switch port is mitigated.