Register for Federated SSO
The company administrator for your organization must register for Federated Single Sign-On (SSO). Use the procedures below to provide the necessary information and to connect your company Identity Provider (IdP) to Equinix.
To register your organization for Federated SSO:
-
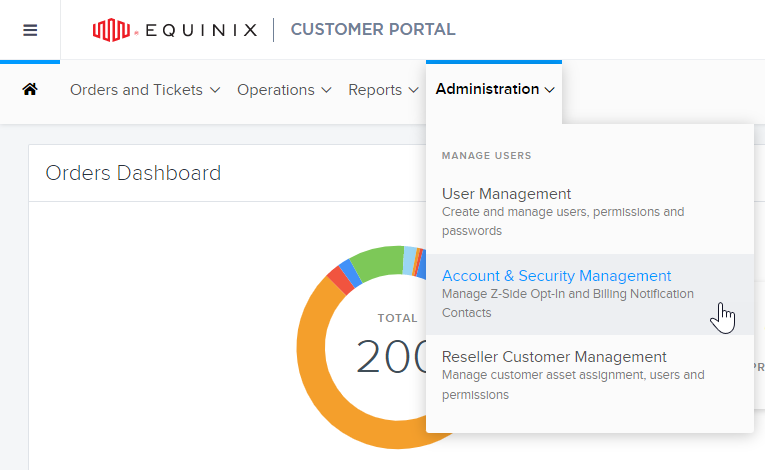
From the Administration menu in the Customer Portal, click Account & Security Management.
-
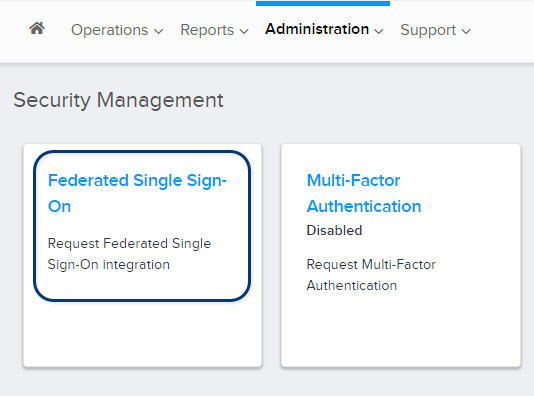
Click Federated Single Sign-On.
-
On the Federation Registration page, read the instructions for the set-up process and click Next.
Metadata Details
On the Metadata Details page enter your organization's email address domain. If you have multiple domains, separated them with a comma.
acme.com, eu.acme.com
Next, provide the metadata in one of two ways:
-
Upload your SAML file. This method automatically enters the required information. Important: Equinix requires a user email address in the SAML response. All other attributes are ignored.
noteWith this method, the Entity ID, SSO URL, and Identity Location fields are disabled and you cannot edit them. To change these fields, click Discard, then import an updated SAML file (or enter the information manually, as described below).
-
Manually enter SAML information.
- Entity ID – Enter the entity ID for your organization. Ask your company's identity administrator for the value for this field.
- Single-Sign-On URL – Enter the IdP URL where Equinix will post the SAML request. Ask your company's identity administrator for the value for this field.
Click Next.
Technical Contact Information
On the Technical Contact page, indicate the Point of Contact between your organization and Equinix. Select either Internal or External:
- Internal (default) – Select an existing Equinix-registered user within your organization.
- External – Add a user as the point of contact who is not a registered user; enter the first name, last name, email address, and phone number.
Typically, the Identity Administrator from your organization may be interested in setting up this SAML configuration with Equinix.
Click Next
Certificate Upload
On the Certificate Upload page, if your certificate is not part of the SAML data, then upload it here.
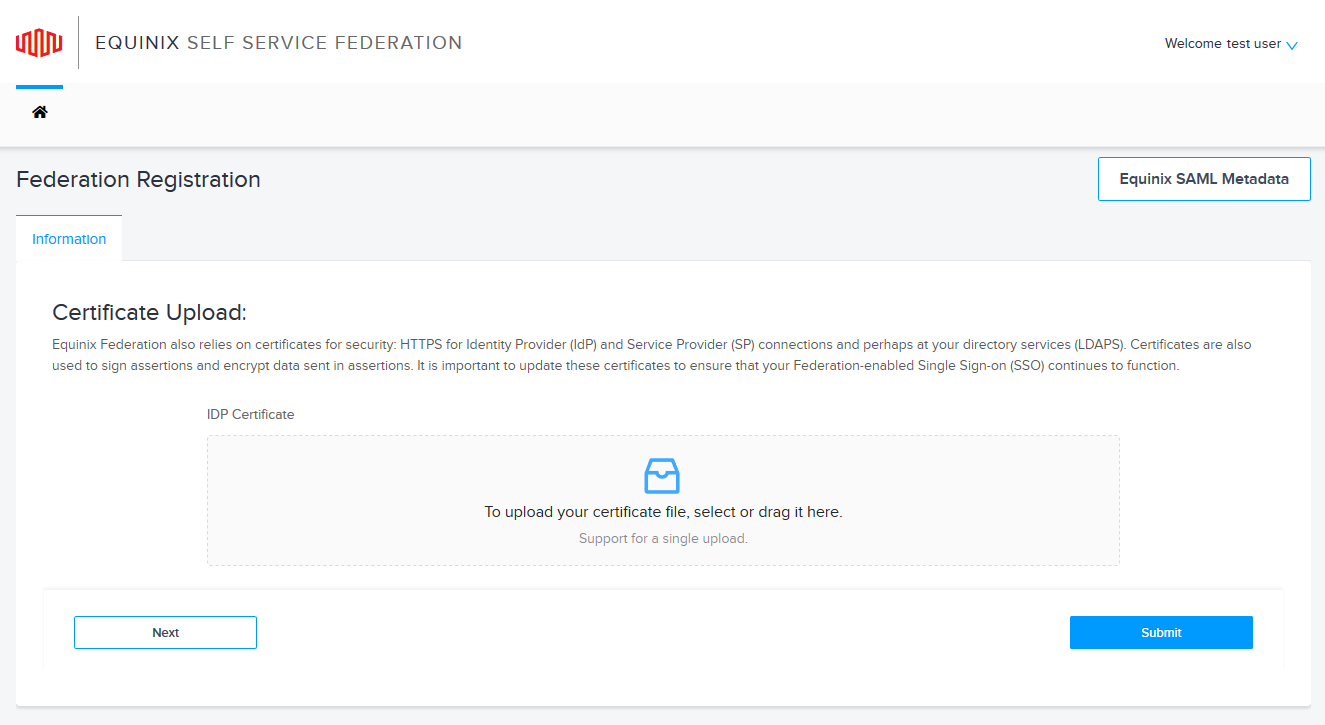
Equinix uses this certificate to validate the authenticity of the SAML requests that originate from your organization.
Equinix verifies the certificate end date; expired certificates are not accepted.
Click Submit.
Registration Status
The Federation Details page shows the Provisioned Status as Submitted.
Once your request is submitted:
- The Equinix Administrator reviews your submitted information and contacts you if further information is required.
- You can see the comments entered by the Equinix Administrator on your request page.
- During this process, you will receive emails to update you on the progress.
You can update your request as long as the Equinix administrator doesn't process and approve it.
Click Equinix SAML Metadata to download Equinix metadata and follow your identity provider's instructions to set up Federated SSO integration.
Once you receive an email that your Federated SSO request has been approved, verify that you can log in to Equinix portal.
Verify Federated SSO Configuration
When the Federated SSO configuration is ready and your request is in PROVISIONED status, validate your Federated SSO setup.
-
Go to portal.equinix.com.
-
Click Sign In with SSO, then provide your email address and click Continue.
-
Enter your login credentials to authenticate and access the Equinix portal.
infoIf you're unable to log in, add a comment to your federation request to engage with Equinix administrator and troubleshoot your login issues.
-
Go to your federation portal using the link in the email or through the Customer Portal.
-
Under Portal URLs, click I have verified that the federation single sign-on is working for all applications.
-
Click Confirm.
An email notification is sent with a confirmation that the processing of your Federated SSO request has been completed.
List of Federation Statuses
Provisioning statuses that you might see during the process:
- SUBMITTED – The application registration request has been submitted and is being reviewed by the Equinix Administrator.
- AWAITING RESPONSE – The Equinix Administrator needs additional information to process the request.
- IN-PROGRESS – Provisioning is in progress.
- PROVISIONED – The application is provisioned in all systems.
- COMPLETED – You have tested the application and the request is closed.