Access Network Edge Devices
Network Edge devices can be accessed using the Web-based console from the Equinix Customer portal or using the terminal emulation tool with Secure Shell (SSH) protocol. This document discusses how to access devices using those tools.
Availability of Web console/SSH access depends on vendor implementation. See the Device Configuration section for vendor-specific options.
Network Edge Device Access Options
| Device Type | Available Options |
|---|---|
| Equinix-Configured (End of Sale) | User is authenticated through the user-defined SSH credentials created through the Equinix Customer portal (Up to 5 local user accounts can be created through the portal) |
| Self-Configured | Temporary password is randomly generated during the device deployment process. |
| Public/Private key pair can be used for secure password-less SSH authentication |
For self-configured devices, you are strongly advised to change your portal-generated temporary password after initial access using SSH or Web Console. You will have the option to configure additional authentication mechanisms after the initial provisioning phase, based on your business requirement.
Manage Temporary Password
A temporary password is generated for initial device access purposes when a Self-Configured device is initially provisioned. You are strongly advised to change this temporary password by setting another password for a given username. When a different and unique password is configured on the device, you can delete this temporary password generated on the portal by clicking the delete icon in the Temporary Password section of Device Details. Click the icon to show/hide the temporary password or copy the temporary password.
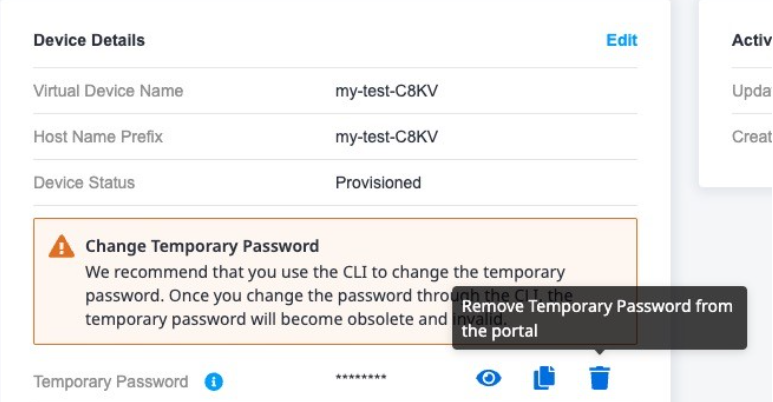
Once the temporary password is removed, the action cannot be reversed.
Access Network Edge Device Using Web-Console
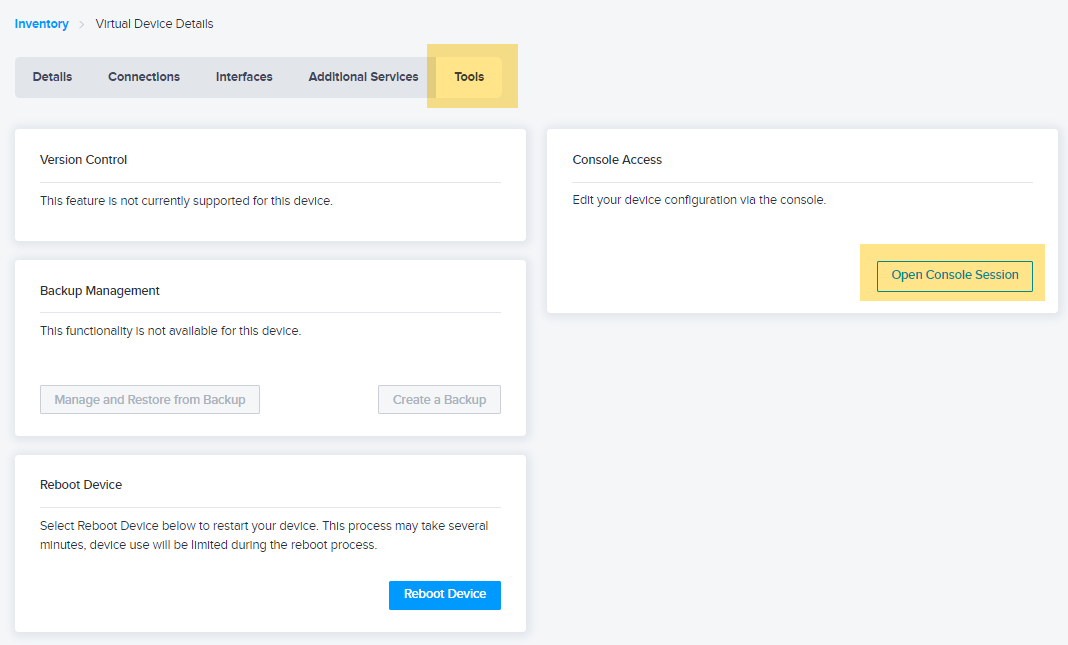
Web-based console access is available through a secure HTTPS session on the Equinix Customer portal (Web-Console). Once you have logged in to the Equinix Customer portal, the console is accessible by going to Virtual Device Inventory, selecting your device, and clicking Tools. In the Console Access card, click Open Console Session.
Web-console access options:
| Configuration Type / Deployment Type | Equinix-Configured Device | Self-Configured Device |
|---|---|---|
| Single Device Deployment | User-defined password | Temporary password |
| Redundant Deployment | User-defined password | Temporary password |
| Cluster Deployment | N/A | Temporary password |
The Copy and Paste operations are not supported when using Web-console access. You have to manually enter the credentials when prompted.
Access Network Edge Device Using SSH Protocol
Network Edge devices can be accessed using Secure Shell (SSH) Protocol. For Equinix-configured devices, you can log in through the local user account created on the Equinix Customer portal during device creation.
Up to 5 local user accounts can be created through the portal.
For self-configured devices, you can access devices using SSH protocol with a temporary password or RSA Public/Private key pair configured during device creation for password-less authentication. You need to change your temporary password after initial log in.
SSH access options:
| Configuration Type / Deployment Type | Equinix-Configured Device | Self-Configured Device |
|---|---|---|
| Single Device Deployment | User-defined password | Public/Private key pair or temporary password |
| Redundant Deployment | User-defined password | Public/Private key pair or temporary password |
| Cluster Deployment | N/A | Public/Private key pair or temporary password |
Create Local SSH User for Equinix-Configured Devices
If Equinix-configured device type is selected, the Equinix Customer portal allows you to select and create a local username and password for the Network Edge device.
- Go to Additional Services, and on the Add Users card, select the Primary Device check box.
- Select a user from the Existing SSH Users list or click Add New SSH User to configure a new user name and password. This new account will be used to access the Network Edge device with SSH protocol.
The Equinix-Configured device type has reached End of Sale and is no longer available for new customers. Deploy the Self-Configured device type for more flexibility.
Allow SSH Protocol Access for Network Edge Using Access Control List
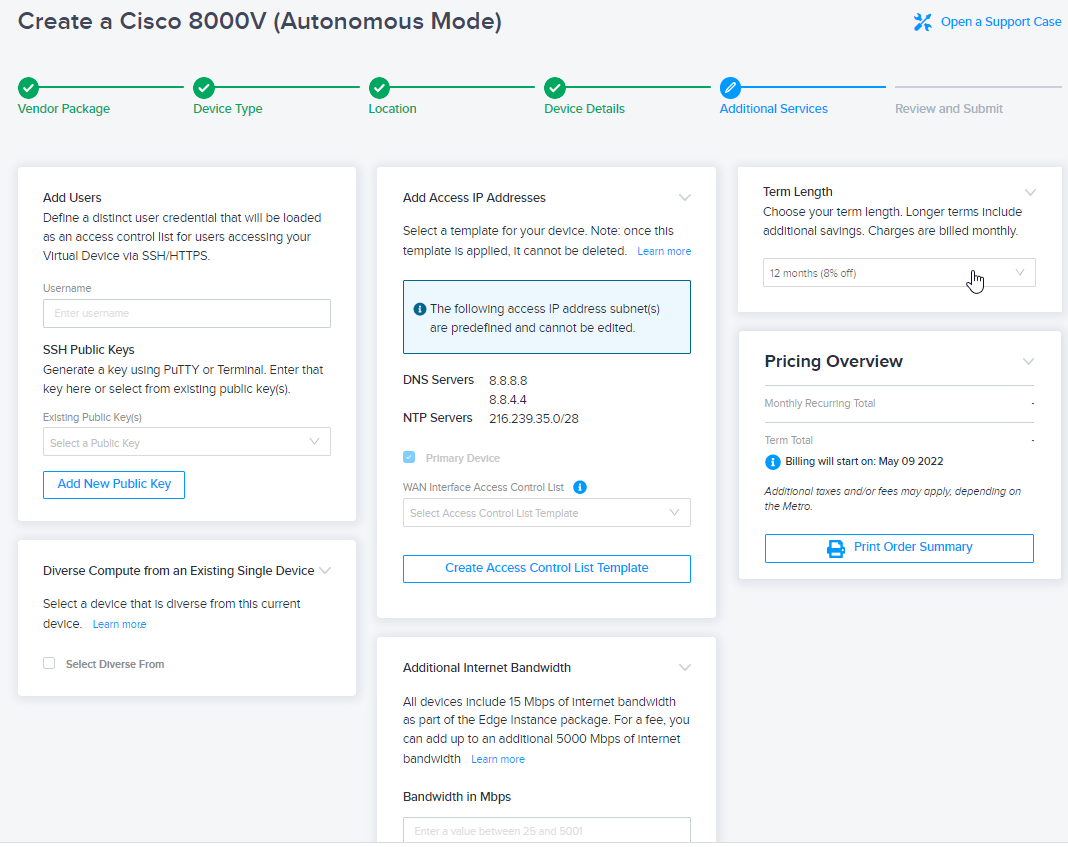
Any external traffic to a Network Edge device through the Internet-facing interface is denied by default. To access a device using SSH protocol, a traffic-specific Access Control List (ACL) needs to be applied in the Equinix Customer portal.
-
Go to Additional Services, and on the Select Access Control List card, click Edit and select the Primary Device check box.
-
In the WAN Access Control List drop-down menu, select an ACL template. Or, click Create Access Control List Template to configure a new ACL.
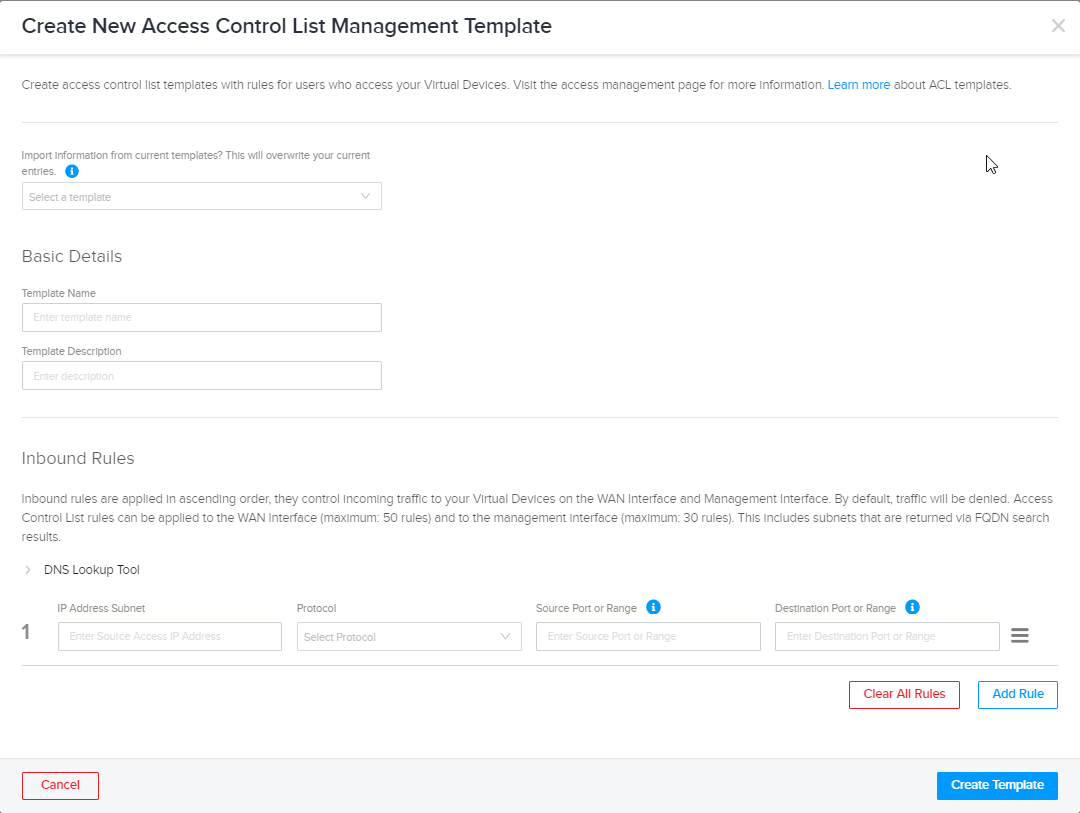
The new ACL needs to permit SSH protocol. You can configure a specific source IP address subnet and select TCP (protocol) and 22 (Destination Port or Range) for SSH protocol.
SSH Access for Self-Configured Devices
RSA Public/Private Key Pair option:
You will access self-configured devices on Network Edge devices using an SSH Public/Private key pair. To configure this option.
- Generate an RSA public/private key pair on your client system (such as Windows, MAC, or Linux).
- Provide the public key on Equinix Customer Portal for the Network Edge device during provisioning.
- Apply an ACL to permit SSH traffic on Network Edge device.
- Access the Network Edge device using SSH without a password.
To configure using the temporary password option:
- Provide a user name during device creation on the Equinix Customer portal. A temporary password is automatically generated and available on the portal in the Device Details section.
- Access the Network Edge device using SSH with the user name and temporary password
- Change the temporary password after the first use.
Generate an SSH Key Using PuTTY on Windows
-
In the PuTTY Key Generator window, click Generate. Key length of RSA 2048 bits or longer recommended. Equinix recommends patching any terminal application to access VNFs for any type of vulnerabilities.
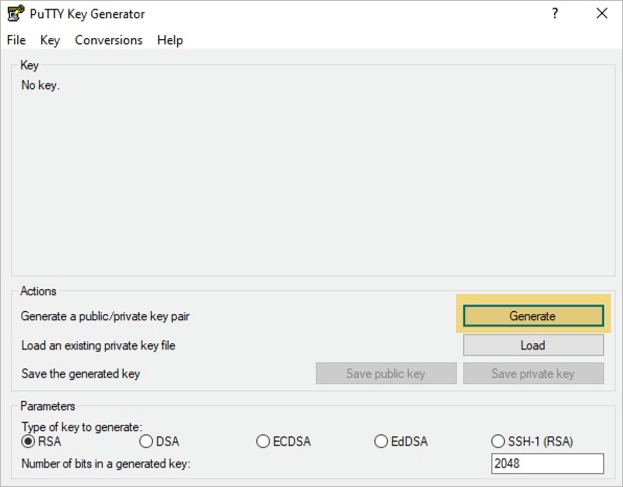
-
Hover over the gray space to generate the keys.
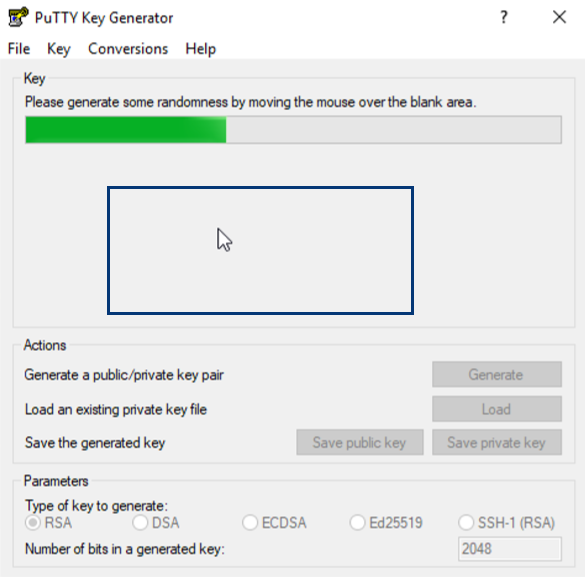
-
Click File in the menu bar and select Save Public Key.
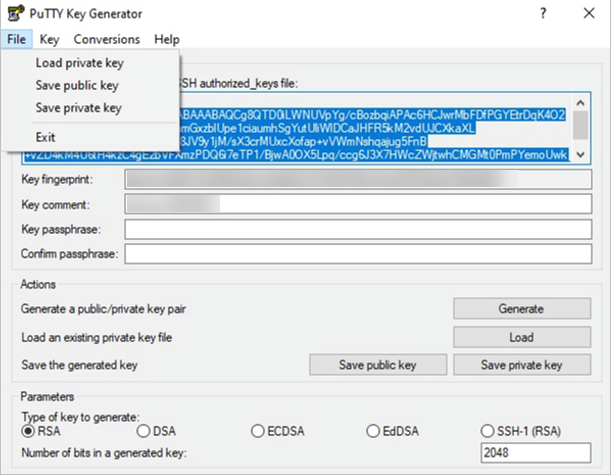
-
Save the public key
<key_name>.pub. -
Save the private key
<key_name>.ppk.
Follow industry guidelines to harden SSH. See Architecture and Configuration for Hardened SSH Keys for the guidelines from NIST (National Institute of Standards and Technology).
Generate an SSH Key on Mac
- Go to Applications, select Utilities, and launch Terminal.
- In the terminal window, enter
ssh-keygen -t rsa. - Press enter on your keyboard to accept the default directory
/Users/user_name/.ssh/. - (Optional) Enter the passphrase to encrypt private key. It is recommended you use a strong passphrase to protect the private key, but you can press enter to leave it empty.
Two keys will be created in /Users/user_name/.ssh/ directory. The username will be your MacOS username. The two keys created are:
- id_rsa (Private key file)
- id_rsa.pub (Public key file)
-
Enter
cat ~/.ssh/id_rsa.pubto display your public key. -
Copy the section of your output highlighted in the image below.
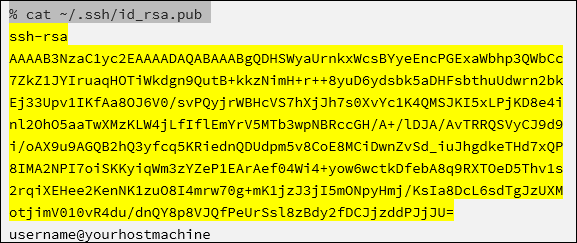
-
During the device creation process, paste the output in the Public Key field in the Add New Public Key section of Additional Services.
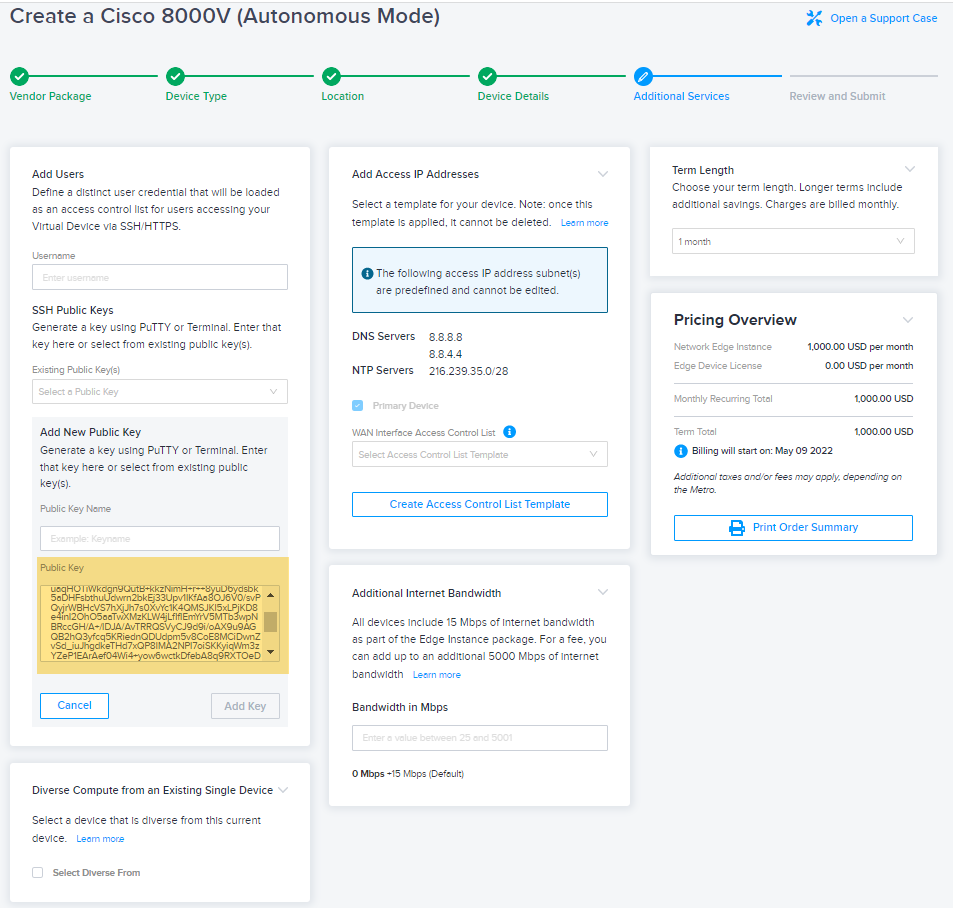
-
Enter a name for the public key and click Add Key.
-
Make sure you apply your ACL to allow SSH traffic on the device interface. See Allow SSH Protocol Access for Network Edge Using Access Control List above.
Access Network Edge Device using SSH with Private Key
-
Locate the Fully Qualified Domain Name (FQDN) or IP Address of your provisioned Network Edge device.
- Go to Virtual Device Inventory and click your device.
- Click Details and scroll to IP Address or FQDN.
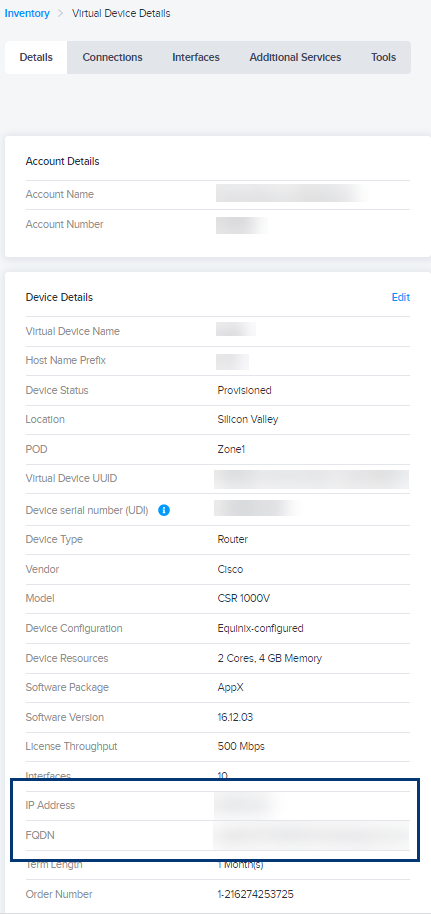
-
Use a terminal emulation app to SSH to your device.
-
Enter
ssh your_username@your_ne_fqdn_or_ip_addressto access your Network Edge device.If you used a passphrase to encrypt your private key, you might be prompted to type the passphrase to log in to your device.
Troubleshoot Your SSH Session
Check the following points if your SSH Public/Private key access is not working.
- Make sure your Network Edge device is provisioned completely. Your device status should be
and you should be able to see all interface information.
- Make sure your ACL allows SSH protocol.