The Primary Interface ACL service enables users to enter one or more IP address blocks that are allowed (or ALLOW in route filtering lexicon) to access the primary interface enabled on all devices. software stack and major components of the OSS/BSS, as well as the “packet walk” from virtual devices to the cloud and other destinations are covered.
The ACL operates in a traditional manner to other well-known network device ACLs. You should always have at least one IP address block if:
- You intend to access the device directly using SSH, web GUI, or other means.
- Your device is controlled and managed by SaaS or any other software package or third-party software, such as with an SD-WAN device. Vendor guidance should indicate which addresses are needed.
- You intend to pass any traffic to the device through the public internet interface.
- You want to enable VPN Tunnels from the device to remote locations over the public internet.
Equinix automatically has basic access to the device, but without enabling at least one block of allowed addresses, these actions won’t work for customers outside the Equinix operations. Once an address is entered, Equinix orchestration enables this allow list in multiple locations:

This includes, but is not limited to:
- Interfaces on the public gateway router for public internet access
- Top of rack interfaces facing the GW routers
- Primary or internet interface on the VNF
- Select troubleshooting and operations tools
The primary interface ACL service has the following attributes:
|
Values |
Data Requirements |
Notes |
|
|---|---|---|---|
|
Configure before launch |
No/NA |
||
|
Configure at launch: |
Yes |
On the Additional Services section of the new device. |
|
|
Configure during lifecycle: |
Yes |
On the Additional Services section of device details. |
|
|
Optional or Required |
Optional |
Might be required on some devices, see device profile or details for more information. |
|
|
IP Address |
x.x.x.x/y |
IPv4 address in numeric format; where X is min 0 and max 255, and y is min 1 and max 32 |
The system blocks 0.0.0.0/0; system doesn’t validate or verify address blocks or ownership against an IRR at this time; can be public or private. |
|
Device |
UUID; Required |
alphanumeric |
On the portal, the device UUID is assumed based on the currently active device that user is viewing. |
|
How many IP blocks per device |
50 |
||
|
How many IP addresses per account |
Unlimited |
NA |
|
|
Max CIDR/Subnet size |
None |
/1 or smaller; system blocks /0 |
|
|
Reqd same on secondary? |
No |
Can have the same or different. |
When adding this service to an redundant pair, you must specify whether you want the same set of IP addresses added to the secondary device. You can also specify a different list.
Equinix maintains a TACACs server that allows SSH users to access devices from allow listed IP addresses, and from Internet backbone routers. This service informs Equinix infrastructure which IP addresses and subnets are allowed to access the device. This service works for both individual users through an SSH client as well as 3rd party software, applications, or orchestration that manage the device. It's for this reason that a user might need to configure this service even if they have no users defined, such as:
- An SD-WAN device where external SaaS manages access
- A network performance software package that captures SNMP traps through the SSH interface
- Third party software or orchestration that controls this device
- Many other possible scenarios
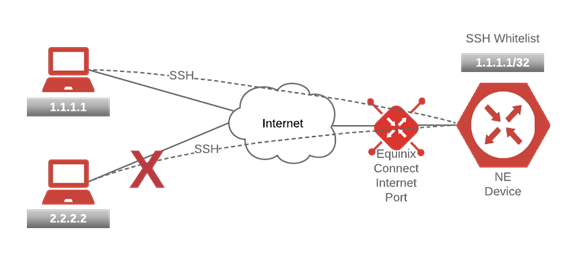
Although the blocks are limited to 50, the user can effectively enter a large number of concurrent addresses if needed when accounting for the subnet. The system restricts some entries (such as a “permit all” 0/0 entry, and some private address space). At any time during the lifecycle of the device, users can add to or remove from this list.
Warning: When Save is clicked, the configuration of all allowed addresses is pushed to the device. If this includes the removal of or changes to an address, service is interrupted for anyone associated with that address attempting to access the device.
All users listed in the User Access service are able to access the device from all addresses listed in this service. Equinix recommends that you add as few permitted addresses as possible in as small a subnet as possible. Users should consult with their corporate IT organization to determine the likely origin addresses of those people or systems that need to access the device. Individual users can use a service like whatsmyip to determine the public address you are configuring from on your computer or terminal.
Equinix does not validate ownership of the entered IP subnets with any registry such as ARIN. All traffic from these addresses is solely the customer's responsibility.

